Citrix Bleed 2: what is happening and how your organisation can respond quickly
In recent weeks, a critical vulnerability has been discovered in the widely used remote work system Citrix NetScaler(ADC or Gateway). This vulnerability, known as Citrix Bleed 2 (CVE-2025-5777), allows attackers to gain access to systems via active sessions without requiring login credentials or multi-factor authentication (MFA). It has now been confirmed by, among others, the Dutch National Cyber Security Centre (NCSC) and the Digital Trust Centre (DTC) that this vulnerability is actively being exploited. As a result, thousands of organizations worldwide are at risk.

The impact is also visible in the Netherlands. On July 17th 2025, the Public Prosecution Service (OM) announced that external attackers may have gained access to sensitive systems via this vulnerability. As a precaution, the OM took all of their NetScaler systems completely offline. This meant they temporarily lost access to essential digital infrastructure, such as internal documents, email systems and certain legal case files. Such a measure highlights the severity of the situation: shutting down systems is a drastic, yet sometimes necessary step to prevent further damage.
Wat does this mean for your organization?
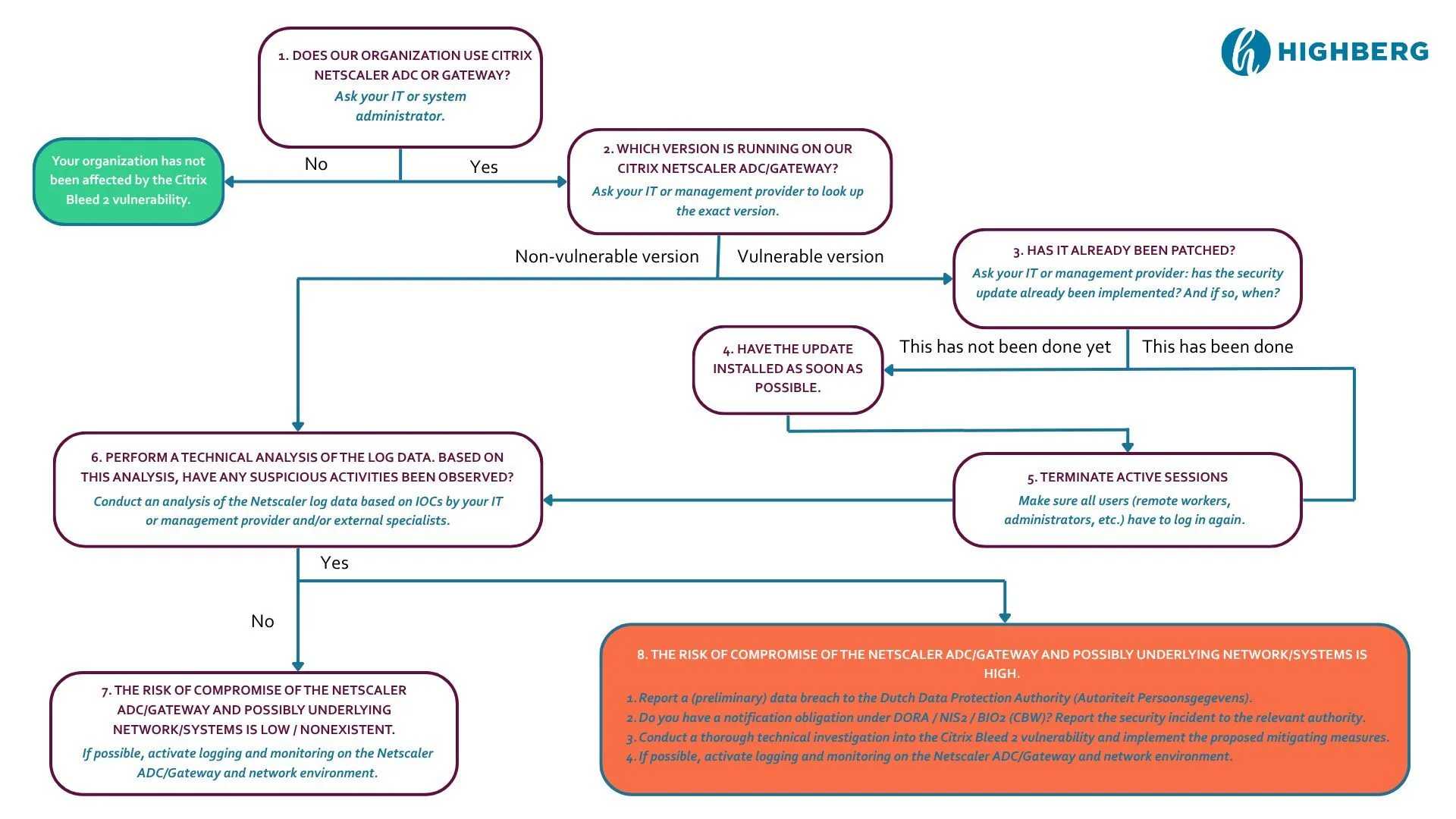
What does this mean for your organization? Does your organization use Citrix NetScaler ADC or Gateway for remote access to systems for, for example, working from home, load balancing or remote management? If so, it is crucial to immediately assess whether you are or have been vulnerable and whether additional measures are necessary. Start by asking the following questions within your organization:
Does your organization use Citrix NetScaler ADC or Gateway?
NetScaler is a product by Citrix and is commonly used to enable secure remote access via portals. If your organization does not use this product, this specific vulnerability does not apply to you. However, if you do, it is important to quickly take the following steps.
Check the version
Not all versions of Citrix NetScaler ADC or Gateway are vulnerable to this attack. Only certain versions contain the vulnerability (< 14.1-43.56 and < 13.1-58.32). Ask your IT administrator or provider which version is currently in use. If your organization turns out not to be vulnerable, we still recommend reviewing log files for any suspicious activity. Also check your backup logs, as active logs may have been altered. Implement continuous monitoring, which reduces the risk of future incidents.
Has it been patched? And if so, when?
If your organization is using a vulnerable version, it is important to determine whether and when it was patched. Patching refers tothe installation of a security update. Without this update, the system remains vulnerable to attacks. If it has not yet been patched, this should be done immediately.
If it has been patched, verify the date: if the update was applied after July 8th 2025, the risk of compromise of the NetScaler ADC or Gateway and potentially underlying networks/systems is very high.
Terminate all active sessions
After patching, it is essential to terminate all active sessions. This means that all users (such as remote workers and administrators) must log in again. Why? Malicious actors may have obtained session tokens or login credentials before the patch was applied. By terminating all connections, any unauthorized access is effectively blocked and attackers are forced to re-authenticate, which they cannot do if the vulnerability has been addressed.
Investigate for signs of exploitation or attempted attacks
Have a scan or investigation carried out to determine whether there are signs of exploitation. Request the Indicators of Compromise (IOCs) from Citrix and check your systems for their presence. This can be done by your internal IT department or, if preferred, by an external specialized firm.
Watch for signs such as unusual login attempts, multiple IP addresses associated with a single user or attempts to bypass multi-factor authentication (MFA).
If suspicious activities are found, it is important to act quickly:
- Report a (potential) data breach to the Dutch Data Protection Authority (Autoriteit Persoonsgegevens).
- Do you have a reporting obligation under DORA, NIS2 or BIO2 (CBW)? If so, report the security incident to the relevant authority as soon as possible.
- Conduct a thorough technical investigation into the Citrix Bleed 2 vulnerability and implement the recommended mitigation measures.
- If possible, enable logging and monitoring on the NetScaler ADC/Gateway.
Continue monitoring
If no suspicious activity has been detected, the risk of compromise of the NetScaler ADC or Gateway and any underlying networks and systems is low or non-existent. It is recommended, if possible, to implement continuous logging and monitoring on the NetScaler ADC or Gateway and the network environment.
TIP: Create an overview of external vendors with access to your systems
Check whether they use any of the vulnerable systems mentioned and go through this decision tree together with them to determine whether further action is required.
The information has been created with the greatest possible care. Nevertheless, Highberg cannot guarantee the completeness, accuracy, or timeliness of the information provided. The content is intended for general informational purposes only. No rights can be derived from this information.
Support and advice from Highberg
If your organization needs support in conducting (technical) analyses, reporting and handling a security incident and/or data breach or implementing security measures, please contact Highberg’s security department. Our services help protect organizations against threats, enhance their resilience and ensure compliance with regulatory requirements, creating a secure and compliant operational environment.
Want to know more? Get in touch with Arjen Bol via arjen.bol@highberg.com or 079 368 1000.
Gerelateerde Insights
